The benefits of application rationalization—more efficient systems, better interoperability, and reduced infrastructure and operational costs—are vital, but an increasingly fundamental benefit in healthcare is that application rationalization thwarts cyberattacks.
Healthcare providers are sitting on a mountain of PHI, where data vulnerability is an immense and growing issue. Healthcare systems with data breaches face operational glitches, fines, and worse, vulnerability around patient safety and disruption of care.
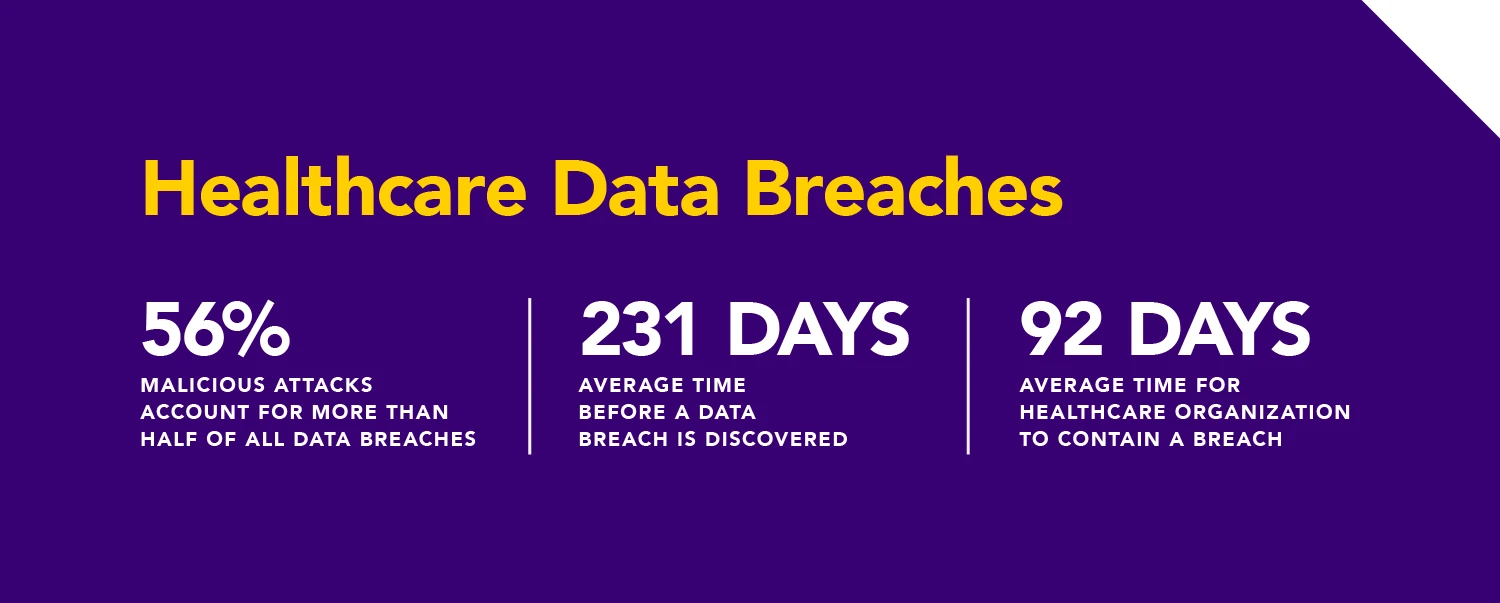
A Growing Problem
Cyberattacks on hospitals have increased by nearly 50% since 2020, making the industry the biggest target, according to U.S. government data and a 2022 analysis from credit rating agency S&P.
Often, the goal of hackers is the installation of ransomware—a type of malware that holds a victim’s data or device hostage, threatening to keep it locked (or worse) unless the victim pays a ransom to the attacker.
If they don’t get paid, hackers start releasing stolen PHI on the dark web, making providers vulnerable to personal lawsuits. Targets for cyberattacks are moving downstream, from large healthcare systems to mid-sized providers whom hackers suspect are less prepared.
According to Statista, the average cost of a data breach in the U.S. in 2023 was $9.4 million.
Systems Are the Root of Cyber Vulnerability
Why are healthcare providers so often the target of cyberattacks? The answer is that their systems are often outdated and vulnerable. A HIMSS survey found that 73% of healthcare organizations still operate legacy systems. Some systems are so old, that current IT employees don’t know how to protect them. Most systems are not hosted in the cloud, which by its nature provides some cybersecurity protection.
And old systems take time to fix. John Riggi, the American Hospital Association’s national advisor for cybersecurity and risk, said the recovery process can take weeks, with hospitals in the meantime reverting to paper systems and humans to do things such as monitor equipment and run records between departments.
Application Rationalization Offers Six Lines of Defense Against Cyberattacks
Application rationalization in healthcare organizations involves assessing, streamlining, and optimizing the application portfolio to enhance efficiency, reduce costs, and mitigate risks, including cybersecurity threats. Here’s how it also helps protect healthcare organizations from cyberattacks:
- Reduced Attack Surface. By eliminating redundant or outdated applications, healthcare organizations reduce their attack surface—the number of potential entry points for cybercriminals.
- Improved Security Posture. By consolidating applications into a smaller, more manageable set, healthcare organizations can more effectively allocate cybersecurity resources, such as implementing robust access controls, encryption, and monitoring mechanisms.
- Easier Patch Management. Application rationalization simplifies this process by reducing the number of applications that require updates. This ensures that critical security patches are applied promptly, reducing the likelihood of exploitation by cyber threats.
- Better Compliance Management. Rationalizing applications can help ensure compliance with HIPAA regulations by reducing the number of systems that need to be audited and maintained in accordance with regulatory standards.
- Enhanced Monitoring and Detection. Security teams can more effectively detect unauthorized access attempts, unusual data transfers, or other signs of potential cyber threats across a streamlined set of applications.
- Streamlined Incident Response. In a rationalized system, security teams can quickly identify and isolate affected systems, contain the breach, and restore operations with minimal disruption, as they have a clearer understanding of the organization’s application landscape.
Reduce Cybersecurity Threats and Cut Costs at the Same Time
Application rationalization can ultimately drive cost savings, too. The typical healthcare organization spends 8.1% of their total IT budget on cybersecurity. This investment can be reduced by making the entire IT landscape more secure following application rationalization.

